How to know if the Ubuntu image you have launched has addressed a specific CVE?¶
This guide will help you determine if a running Ubuntu instance has addressed a specific CVE that you are interested in. We’ll heavily rely on the Ubuntu OVAL tooling developed by the Canonical Security Team to address this question.
To follow the instructions given below, you’ll need some sort of command line access to your instance, e.g. SSH.
Install the required packages¶
Install the required packages - bzip2 (to uncompress the OVAL data) and OpenSCAP (to scan the instance):
sudo apt update && sudo apt install libopenscap8 bzip2 -y
For more information about OpenSCAP(oscap) tooling check out Documentation for OpenSCAP Base.
Scan the instance¶
The following commands will:
Retrieve the name of the Ubuntu release running on your instance
Download the CVE OVAL feed for that release
Extract the XML file from the downloaded archive
Scan the instance, i.e. use the
oscaptool to run an OVAL evaluation using the downloaded OVAL feed
export $(cat /etc/os-release | grep UBUNTU_CODENAME)
wget "https://security-metadata.canonical.com/oval/com.ubuntu.${UBUNTU_CODENAME}.cve.oval.xml.bz2"
bunzip2 "com.ubuntu.${UBUNTU_CODENAME}.cve.oval.xml.bz2"
oscap oval eval --report report.html "com.ubuntu.${UBUNTU_CODENAME}.cve.oval.xml"
Download the scan report¶
The scan report will be available on your instance as report.html in the directory where you ran the scan (oval eval). You can download it to your local machine using a file-copying tool such as scp or rsync, and if you open it in a browser you’ll see something similar to:
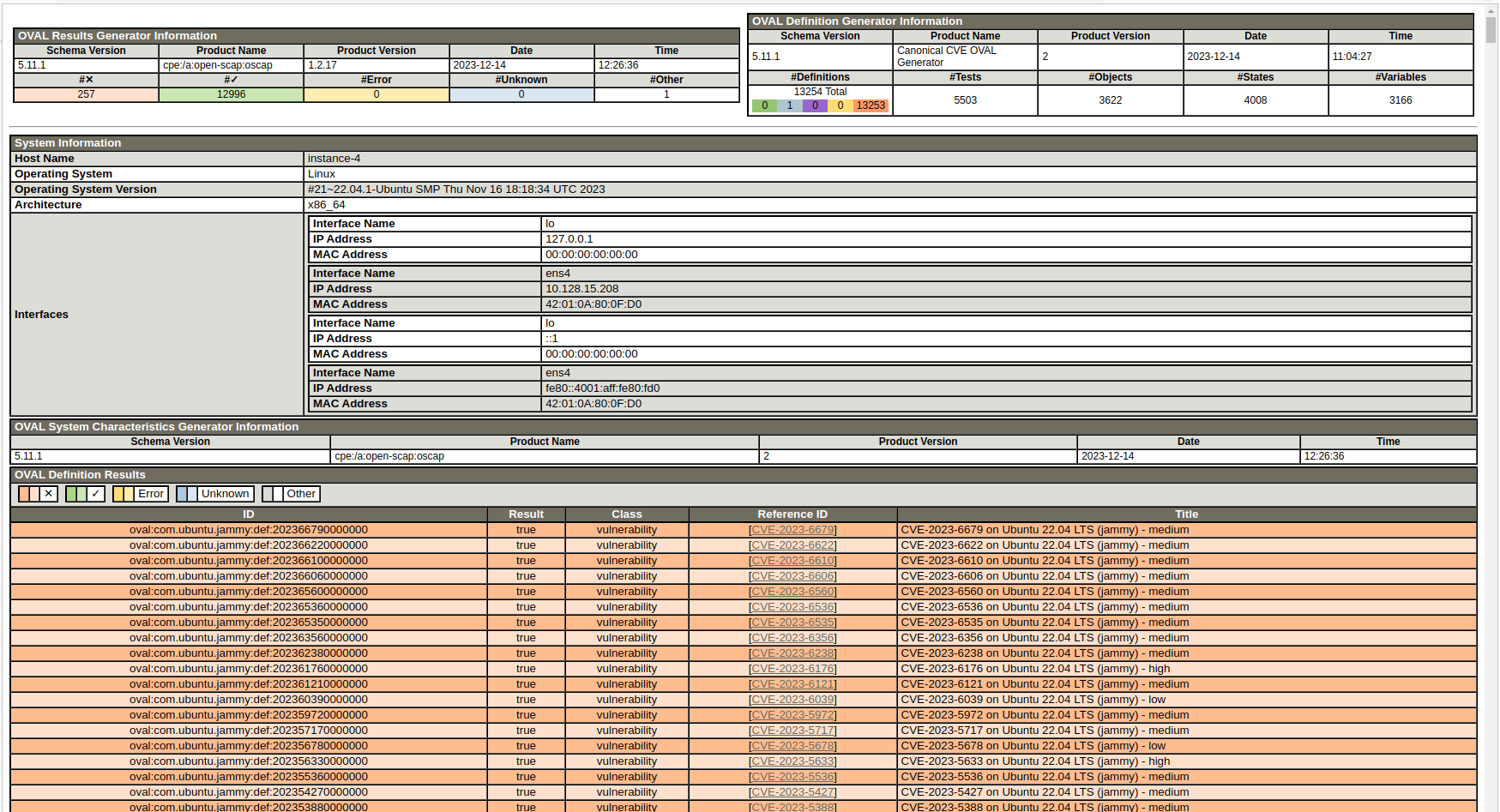
You can check the Reference ID column of the results table for the specific CVE that you are interested in. The color code indicates if the CVE is addressed on your instance in its current state. A green row indicates an addressed CVE while an amber one indicates otherwise.
